Imagine If You Could Monitor the Available Cargo Space in Every Container and Truck Trailer in Your Fleet
Imagine if you could monitor and assess the available cargo space in every container and truck trailer in your fleet no matter where they are, from your desk through the cloud. Know exactly what cargo is in a container's or trailer's cargo area, its physical profile, its weight profile, the types of cargo it's carrying and its location in the world. Couple this with order entry and logistics routing software in your cloud's Fleet Management Operations Center and you could more than double the efficiency of those assets. This should translate into more than twice the number of turns per asset annually. Simplistically, double your revenue or cut your operating expenses in half and double your profits. Do more with less!
Highly-Metalized-Environment (HME) Sub GHz Ultrasonic Sensors, like those from ThinkTec, coupled with a wide-area-network Communications device and Cloud Data Sharing make this a reality, now! Container and Truck Trailer cargo areas are equipped with Ultrasonic Sensor Networks on both their left and right walls. A Left-wall Ultrasonic Sensor Network is illustrated below.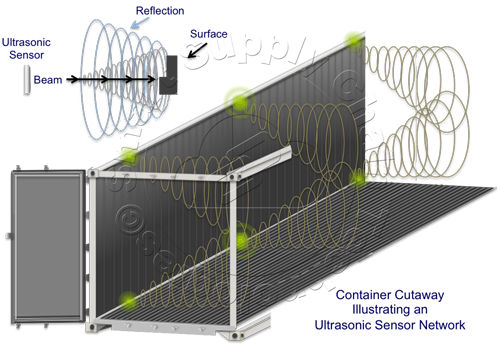
Each Ultrasonic Sensor periodically emits an ultrasonic signal and receives its reflection after it bounces off the surfaces of the cargo. When these Ultrasonic Sensors are connected together to form a network, managed by a central Master Processing Unit, a very precise image can be constructed from the combined signals reflected from the surfaces of the cargo in the covered area. These reflections are analyzed and organized by 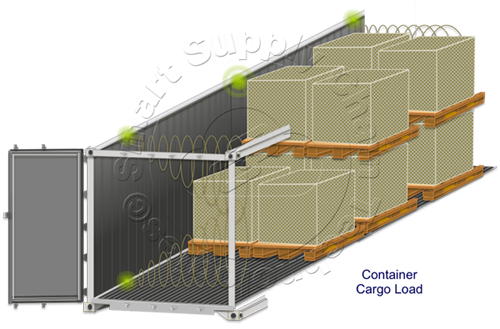 the sensor network's Master Processing Unit and then sent to the container's or trailer's wide-area-network Communication device. The Communications device further analyzes and organizes the data from both the Left-wall and Right-wall networks and sends that data to the asset's cloud server for further analysis, visual presentation and use. Overarching all of this mission-critical data flying around, within a cargo area and even between a container or trailer and the cloud, must be data protection and security.
the sensor network's Master Processing Unit and then sent to the container's or trailer's wide-area-network Communication device. The Communications device further analyzes and organizes the data from both the Left-wall and Right-wall networks and sends that data to the asset's cloud server for further analysis, visual presentation and use. Overarching all of this mission-critical data flying around, within a cargo area and even between a container or trailer and the cloud, must be data protection and security.
It is critical that data being received by an asset's cloud server be valid and uncompromised before it is acted upon. It is also critical, in this era of the Internet of Things, that security for remote devices and systems be seamless and autonomous. Devices within a container or trailer should authenticate each other before exchanging data. This mutual authentication ensures that the data being generated by the authorized devices within an asset's cargo area is not inappropriately, even clandestinely, being intercepted by other devices. Further, this mutual authentication ensures that all of the data being received and operated upon by Master Processing Units within a given cargo area and eventual by an asset's server comes from authorized devices and no false data was inserted or substituted along the way. Device authentication should be based on random "keys" generated and managed by the devices themselves. Each individual Ultrasonic Sensor, for example, authenticates itself to its Ultrasonic Sensor Network's Master Processing Unit each time it wants to send data and then waits for the Master Processing Unit to acknowledge its successful authentication by then authenticate itself before the sensor actually sends its data. Authentication is closed at the completion of the data transfer and begins anew when the sensor again wants to send data to the Master Processing Unit. All data exchanges are framed by this mutual authentication process, even the asset's wide-area-network Communication device and the asset's cloud server are mutually authenticated each time they exchange data, in either direction.
Mutual authentication is only one element of the necessary data security, additionally; the data itself must be encrypted while in flight, by its source device, before it is wirelessly transmitted to any other device. Ideally, data is encrypted, at its source, using standard but strong data encryption techniques, and remains encrypted until it is eventually decrypted by an asset's cloud server and used. In some cases, it might be necessary that data from sensors be decrypted by Master Processing Units or wide-area-network Communications devices to perform critical intermediate data analysis before being sent to the asset's server. Even this decryption is avoided whenever possible by packetizing the source data such that only one of the packets is designated as data that can be decrypted by intermediate devices preserving the encryption of most of the data. All data from an asset's wide-area-network Communications device is encrypted when in flight to the asset's server.
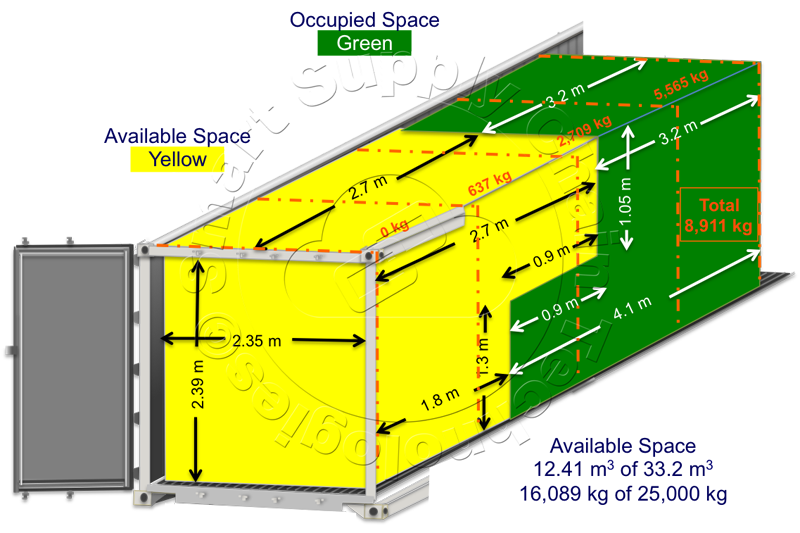 Ultimately, Fleet Management Software running on the asset's cloud server receives data from the cargo area's Ultrasonic Sensor networks, further analyzes the data and generates an accurate profile of the cargo in the cargo area. This physical profile is automatically enhanced with other data from the asset server's database, data from Cargo Monitors that were placed in some of the cargo parcels and data from Data Sharing Partners dynamically retrieved from their databases when required. This combined data produces a detailed profile of the cargo in a container similar to the one illustrated below. The top-level profile shows the cargo's physical dimensions profile and the cargo's general weight distribution across the cargo area's four quadrants.
Ultimately, Fleet Management Software running on the asset's cloud server receives data from the cargo area's Ultrasonic Sensor networks, further analyzes the data and generates an accurate profile of the cargo in the cargo area. This physical profile is automatically enhanced with other data from the asset server's database, data from Cargo Monitors that were placed in some of the cargo parcels and data from Data Sharing Partners dynamically retrieved from their databases when required. This combined data produces a detailed profile of the cargo in a container similar to the one illustrated below. The top-level profile shows the cargo's physical dimensions profile and the cargo's general weight distribution across the cargo area's four quadrants.
The logistics company personnel or terminal operations at a data sharing partner terminal can view this data for any of its cargo carrying assets. These personnel can also drill down into the data to generate a profile of the types of cargo in the "occupied space" and even further to see more precise position and weight for specific cargo that had Cargo Monitors embedded in their packaging as they were packed for shipping. 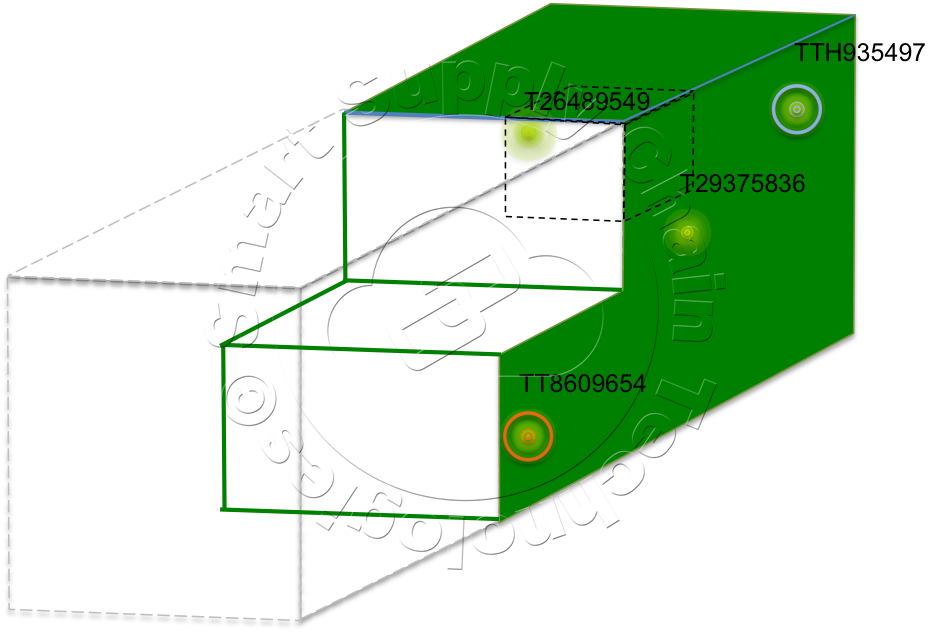 Cargo Monitors can hold all kinds of data, recorded into them before they are packed with the cargo, and can have their own embedded sensors, temperature, humidity and others, that collect data specific to the package they are packed with. Cargo Monitors are an example of a special class of device that does not follow the mutual authentication framework described above. Rather, these devices are treated as non-secure devices that send encapsulated encrypted data along with a unique Tag ID to devices programmed to communicate with them. The primary use for these types of devices is to deliver data to supply chain end-customers like a profile of the temperatures their package encountered along its journey. Devices that do communicate with this class of device simply receive and pass their Tag IDs and their encapsulated data along until it reaches an asset's server. The asset's server places these Tag IDs and data into a "vaulted" storage area on the server until its Fleet Management software determines that if any of the data is useful. Useful Cargo Monitor data is authenticated, to the level possible, using the server's data sharing software across the cloud. The data is retrieved from the vault area and used. Much of this data never leaves the vaulted area and is eventually just deleted.
Cargo Monitors can hold all kinds of data, recorded into them before they are packed with the cargo, and can have their own embedded sensors, temperature, humidity and others, that collect data specific to the package they are packed with. Cargo Monitors are an example of a special class of device that does not follow the mutual authentication framework described above. Rather, these devices are treated as non-secure devices that send encapsulated encrypted data along with a unique Tag ID to devices programmed to communicate with them. The primary use for these types of devices is to deliver data to supply chain end-customers like a profile of the temperatures their package encountered along its journey. Devices that do communicate with this class of device simply receive and pass their Tag IDs and their encapsulated data along until it reaches an asset's server. The asset's server places these Tag IDs and data into a "vaulted" storage area on the server until its Fleet Management software determines that if any of the data is useful. Useful Cargo Monitor data is authenticated, to the level possible, using the server's data sharing software across the cloud. The data is retrieved from the vault area and used. Much of this data never leaves the vaulted area and is eventually just deleted.
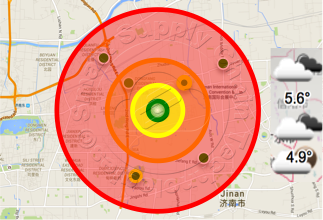 This data can be used by operations personnel, assisted by analytics and routing software running on their servers, to route the container or truck to another location to pick up additional cargo that fits in the available space and weight profile. The analytic software generates a zone profile based on the container's or truck's timeline commitments for the cargo it is currently carrying, the distance to and logistics at other "qualified" cargo pickup locations, traffic and weather conditions, pickup revenue value and other established or on-the-fly criteria. The cargo pickup is selected and automatically reflected in the Fleet Management Center's Logistics System.
This data can be used by operations personnel, assisted by analytics and routing software running on their servers, to route the container or truck to another location to pick up additional cargo that fits in the available space and weight profile. The analytic software generates a zone profile based on the container's or truck's timeline commitments for the cargo it is currently carrying, the distance to and logistics at other "qualified" cargo pickup locations, traffic and weather conditions, pickup revenue value and other established or on-the-fly criteria. The cargo pickup is selected and automatically reflected in the Fleet Management Center's Logistics System.
This is truly a remarkable capability that no logistics company can afford to be without. All of this technology is available today from Smart Supply Chain Technologies and its ever growing partner Ecosystem.